Why Host with Critical Consulting?
When looking to implement or outsource your servers, there are several key factors to consider. Is the service reliable? Are there engineers on standby 24×7 in case a server goes down? Does the service offer the full benefits?
Reliability and Uptime
Our service operates out of a tier-four datacenter, with state-of-the-art cooling, power supply, backup generator and fire suppressants. For you this means that your email is constantly running. Your service will run on clustered servers and an EMC storage area network – so if one server or disk drive stops working, your service keeps working.
As well as offering the highest-quality IT infrastructure, we do nightly backups to protect your data.
24/7 Monitoring and Management
To further ensure reliability, we employ a team of Microsoft engineers and administrators 24/7. So if a server problem occurs at 3am on a Sunday morning, we will be there to solve it – in a matter of minutes. This same team installs Microsoft software patches immediately, as well as anti-virus and anti-spam updates, for full protection.
Better Technologies
One of the world’s most advanced infrastructures:
|
Critical Consulting |
Other Providers |
 |
|
Brand new equipment |
|
|
 Only new, premium infrastructure –never ‘pre-owned’ Only new, premium infrastructure –never ‘pre-owned’ |
 |
 |
|
Dell PowerEdge servers |
| Multicore, multi-processor, all 64-bit |
|
 |
 Less robust ‘no-name’ servers Less robust ‘no-name’ servers |
 |
|
EMC storage area networks |
| Fiber-channel, RAID 10 reliability |
|
 |
Lower-grade SAN, or local disk storage |
 |
|
Multiple tier-4 datacenters |
|
|
Four tier-4 datacenters on West and East coasts |
Single datacenter, typically tier-2 or tier-3 |
 |
|
Multiple tier-4 datacenters |
| For maximum uptime |
|
 |
Lower-cost networking hardware |
 |
|
Multi-layer security |
| Perimeter and on-server |
|
On server + clustered-server perimeter defense |
 |
 |
|
Failover facilities |
| For high redundancy |
|
 |
Single-facility – a high-risk strategy |
INFRASTRUCTURE YOU CAN COUNT ON
The business impact of a service outage or the loss of years’ worth of critical data is incalculable. It is not surprising that service level agreements have become a critical aspect of the Exchange provider selection process. While every provider can talk the talk, the reality is that uptime and data replication is only as good as a provider’s infrastructure and experience.
At Critical Consulting, the premium infrastructure behind our solutions is built on more than a 10 years of Exchange hosting experience. This enables us to offer a 99.999 percent uptime SLA – that’s less than six minutes of downtime per year. To ensure we consistently meet or exceed the service expectations of our users, we never stop investing in infrastructure. Let’s take a closer look at how Critical Consulting’s infrastructure distinguishes us from other hosted Exchange providers.
Tier-4 Datacenters
Critical Consulting’s multiple datacenters are some of the world’s few tier-4 datacenters.
Critical Consulting uses ultra-robust premium facilities to minimize email downtime. The tier-4 category is for facilities “fundamentally immune to planned and unplanned downtime,” according to the Uptime Institute.
Infrastructure
- Environmental control units that give a 100% SLA-guaranteed temperature and humidity within a certain range, plus the most advanced pre-action fire-suppression systems available.
- Raised floors and zone-4 certified for earthquakes.
Security
- All premises are closely monitored and guarded, 24x7x365, with sophisticated pan/tilt CCTV covering every part of the facility and security guards posted at all entrances.
- Access to servers is restricted to a limited number of authorized engineers and security is strictly enforced using the very latest technology, including man-trap technology, motion sensors and controlled ID key-cards.
Power and Cooling
- Dual-feed 12KV power supply from PG&E, plus N+1 redundancy with redundant power feeds.
- Powerware UPS modules and PDUs with static switches on front end and 6 emergency redundant back-up diesel generators.
- Fully-redundant, roof-mounted, 1500-ton, Liebert system with common ducting, plus security via the elimination of water-filled piping from the datacenter space.
- CRAC units in the electrical and UPS rooms.
Connectivity
- Market Post Tower is home to Verizon’s MAE-West facility.
- The West Coast’s most important communications hub, with carriers including AT&T, Global Crossing, Level 3 Communications, MCI/Verizon, Singapore Telecom, Sprint.
- Failover arrangements to two additional Intermedia California facilities ensure constant uptime.
Dell Servers
Critical Consulting has invested thousands of dollars in its infrastructure, which includes premium Dell servers.
- All servers are 64-bit Dell PowerEdge servers, with multiple multi-core processors.
- Adheres to Microsoft best practices for deployments.
- Passive-active cluster server configuration for ultimate resilience, plus seamless failover when a cluster node is unavailable or taken offline for maintenance.
- Redundant and load-balanced servers increase reliability.
EMC Storage
Critical Consulting uses only the best in hardware, including EMC for the most advanced in storage.
INFRASTRUCTURE FEATURES
Critical Consulting’s, super-premium infrastructure ensures our commitment to reliability is rocksolid. Key features include:
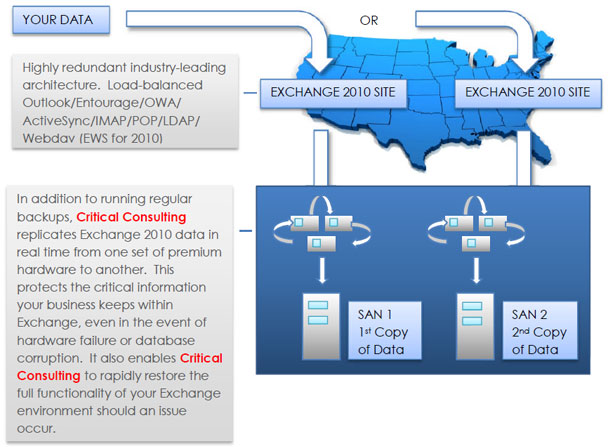
Data replication: In addition to running regular backups, Critical Consulting replicates Exchange 2010 data in real time from one set of premium hardware to another. This protects the critical information your business keeps within Exchange, even in the event of hardware failure or database corruption. It also enables Critical Consulting to rapidly restore the full functionality of your Exchange environment should an issue occur.
Multiple premium datacenters: Critical Consulting operates four premium datacenters in the US, each serviced by multiple Tier-1 Internet providers, including Sprint, Level 3, UUnet (Verizon Business) and Global Crossing. This not only ensures optimal routing to client end points, it enables us to dynamically route around Internet service availability issues.
‘Choose your datacenter’ option: Do you need to support a distributed work force with hosted Exchange services? Critical Consulting lets you choose the datacenter closest to your individual users to ensure your data travels the shortest, fastest route possible.
Multi-million dollar, continually upgraded hardware: Best-in-class servers, storage and network hardware from Dell, EMC and Cisco are the cornerstone of our infrastructure. For example, each datacenter operates redundant Cisco carrier class switches with firewall and load balancing modules. Built for availability and throughput, this flagship technology virtually eliminates disconnects due to server availability or network issues.
- New EMC SAN-based storage with disk clusters in an advanced RAID array for seamless failover.
- Full tape back-ups ensure there no single point of failure anywhere within the storage system.
Premium Network
A premium network from Cisco and other leading vendors ensures the highest possible reliability.
- Routers and switches with full redundancy powered by Cisco
- Netscreen firewalls for enterprise-grade network protection
- HP rack switch technology

















 Only new, premium infrastructure –never ‘pre-owned’
Only new, premium infrastructure –never ‘pre-owned’


 Less robust ‘no-name’ servers
Less robust ‘no-name’ servers